Messenger Upload Failed Make Sure You Are Uploading a Valid File -photo
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical back up.
Employ the Microsoft Intune App Wrapping Tool for iOS to enable Intune app protection policies for in-house iOS apps without irresolute the code of the app itself.
The tool is a macOS command-line application that creates a wrapper around an app. Once an app is processed, you can alter the app'south functionality past deploying app protection policies to it.
To download the tool, see Microsoft Intune App Wrapping Tool for iOS on GitHub.
Notation
If you take issues with using the Intune App Wrapping Tool with your apps, submit a request for assistance on GitHub.
Before you lot run the App Wrapping Tool, you need to fulfill some general prerequisites:
-
Download the Microsoft Intune App Wrapping Tool for iOS from GitHub.
-
A macOS computer that has the Xcode toolset version xi or subsequently installed.
-
The input iOS app must be developed and signed by your company or an independent software vendor (ISV).
-
The input app file must have the extension .ipa or .app.
-
The input app must be compiled for iOS 12.2 or later.
-
The input app cannot exist encrypted.
-
The input app cannot accept extended file attributes.
-
The input app must have entitlements set before being processed past the Intune App Wrapping Tool. Entitlements requite the app additional permissions and capabilities beyond those typically granted. See Setting app entitlements for instructions.
-
To distribute wrapped apps exclusively to your arrangement'southward users, yous need an business relationship with the Apple Programmer Enterprise Program and several entities for app signing that are linked to your Apple Developer account.
To acquire more about distributing iOS apps internally to your organization's users, read the official guide to Distributing Apple Programmer Enterprise Program Apps.
You will need the following to distribute apps wrapped by Intune:
-
A developer account with the Apple tree Programmer Enterprise Programme.
-
In-house and ad-hoc distribution signing certificate with valid Squad Identifier.
- Y'all will demand the SHA1 hash of the signing certificate as a parameter to the Intune App Wrapping Tool.
-
In-house distribution provisioning profile.
Steps to create an Apple Developer Enterprise account
-
Go to the Apple Developer Enterprise Program site.
-
In the top right of the folio, click Enroll.
-
Read the checklist of what you demand to enroll. Click Start Your Enrollment at the bottom of the page.
-
Sign in with the Apple ID of your arrangement. If you don't have one, click Create Apple ID.
-
Select your Entity Type and click Go on.
-
Fill out the form with your organization's data. Click Continue. At this signal, Apple contacts you to verify that you are authorized to enroll your organization.
-
Subsequently verification, click Agree to License.
-
Later on agreeing to license, end past purchasing and activating the programme.
-
If yous are the team agent (the person who joins the Apple Developer Enterprise Program on behalf of your arrangement), build your team first past inviting team members and assigning roles. To learn how to manage your team, read the Apple documentation on Managing Your Developer Account Team.
Steps to create an Apple signing certificate
-
Go to the Apple Developer portal.
-
In the superlative right of the page, click Account.
-
Sign in with your organizational Apple ID.
-
Click Certificates, IDs & Profiles.

-
Click the
 in the meridian right corner to add together an iOS certificate.
in the meridian right corner to add together an iOS certificate. -
Cull to create an In-House and Ad Hoc certificate under Production.

Note
If do not programme to distribute the app, and only want to test it internally, you tin can utilize an iOS App Development certificate instead of a certificate for Production. If you utilize a evolution certificate, brand sure the mobile provisioning contour references the devices on which the app will be installed.
-
Click Next at the bottom of the folio.
-
Read the instructions on creating a Certificate Signing Request (CSR) using the Keychain Access awarding on your macOS computer.

-
Follow the instructions above to create a Document Signing Asking. On your macOS computer, launch the Keychain Access awarding.
-
On the macOS menu at the height of the screen, become to Keychain Admission > Certificate Assistant > Request a Certificate From a Certificate Authority.

-
Follow the instructions from the Apple programmer site to a higher place on how to create a CSR file. Relieve the CSR file to your macOS computer.

-
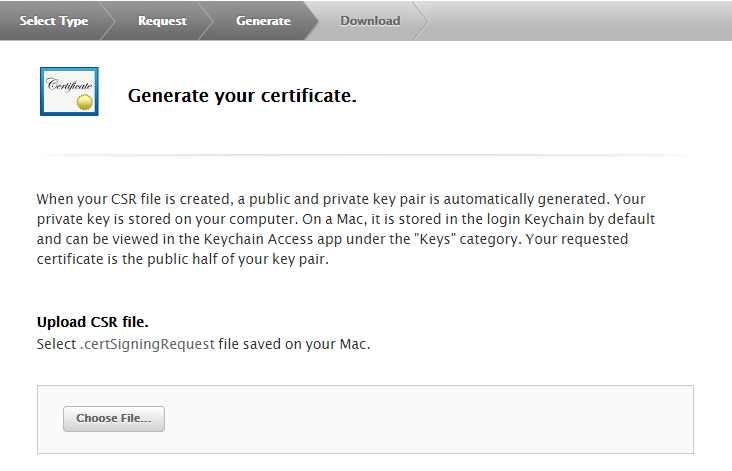
Return to the Apple tree developer site. Click Continue. Then upload the CSR file.
-
Apple generates your signing certificate. Download and save it to a memorable location on your macOS computer.
-
Double-click the certificate file you just downloaded to add together the certificate to a keychain.
-
Open Keychain Access again. Locate your document past searching for its name in the top correct search bar. Right-click on the item to bring upwards the menu and click Get Info. In the example screens, nosotros are using a evolution certificate instead of a production certificate.

-
An advisory window appears. Scroll to the bottom and look under the Fingerprints label. Re-create the SHA1 string (blurred out) to use as the statement for "-c" for the App Wrapping Tool.

Steps to create an In-Business firm Distribution Provisioning profile
-
Go back to the Apple Programmer account portal and sign in with your organizational Apple ID.
-
Click Certificates, IDs & Profiles.
-
Click the
 in the peak right corner to add an iOS provisioning contour.
in the peak right corner to add an iOS provisioning contour. -
Choose to create an In Firm provisioning profile under Distribution.

-
Click Continue. Make sure to link the previously generated signing certificate to the provisioning profile.
-
Follow the steps to download your profile (with extension .mobileprovision) to your macOS reckoner.
-
Save the file in a memorable location. This file will be used for the -p parameter while using the App Wrapping Tool.
-
Download the files for the App Wrapping Tool from GitHub to a macOS computer.
-
Double-click Microsoft Intune Application Restrictions Packager for iOS.dmg. A window with the Stop User License Agreement (EULA) will appear. Read the document carefully.
-
Choose Agree to accept EULA, which mounts the package to your reckoner.
Of import
Intune regularly releases updates to the Intune App Wrapping Tool. Regularly check the Intune App Wrapping Tool for iOS for updates and incorporate into your software development release bicycle to ensure your apps back up the latest App Protection Policy settings.
Use terminal
Open the macOS Terminal and run the following command:
/Volumes/IntuneMAMAppPackager/IntuneMAMPackager/Contents/MacOS/IntuneMAMPackager -i /<path of input app>/<app filename> -o /<path to output folder>/<app filename> -p /<path to provisioning contour> -c <SHA1 hash of the certificate> [-b [<output app build string>]] [-v] [-e] [-x /<assortment of extension provisioning profile paths>] Note
Some parameters are optional equally shown in the following table.
Example: The following case command runs the App Wrapping Tool on the app named MyApp.ipa. A provisioning contour and SHA-one hash of the signing certificate are specified and used to sign the wrapped app. The output app (MyApp_Wrapped.ipa) is created and stored in your Desktop binder.
./IntuneMAMPackager/Contents/MacOS/IntuneMAMPackager -i ~/Desktop/MyApp.ipa -o ~/Desktop/MyApp_Wrapped.ipa -p ~/Desktop/My_Provisioning_Profile_.mobileprovision -c "12 A3 BC 45 D6 7E F8 xc 1A 2B 3C DE F4 AB C5 D6 E7 89 0F AB" -v true Command-line parameters
You tin can employ the following command line parameters with the App Wrapping Tool:
| Holding | How to use it |
|---|---|
| -i | <Path of the input native iOS awarding file>. The file name must end in .app or .ipa. |
| -o | <Path of the wrapped output awarding> |
| -p | <Path of your provisioning profile for iOS apps> |
| -c | <SHA1 hash of the signing certificate> |
| -h | Shows detailed usage information nigh the bachelor control line backdrop for the App Wrapping Tool. |
| -aa | (Optional) <Authority URI of the input app if the app uses the Microsoft Authentication Library> i.east https://login.microsoftonline.com/common |
| -ac | (Optional) <Client ID of the input app if the app uses the Microsoft Hallmark Library> This is the guid in the Customer ID field from your app's listing in the App Registration blade. |
| -ar | (Optional) <Redirect/Reply URI of the input app if the app uses the Microsoft Authentication Library> This is the Redirect URI configured in your App Registration. Typically it would exist the URL protocol of the application that the Microsoft Authenticator app would return to after brokered authentication. |
| -five | (Optional) Outputs verbose messages to the console. It is recommended to use this flag to debug any errors. |
| -due east | (Optional) Utilize this flag to have the App Wrapping Tool remove missing entitlements equally it processes the app. See Setting app entitlements for more than details. |
| -xe | (Optional) Prints information most the iOS extensions in the app and what entitlements are required to use them. Run into Setting app entitlements for more details. |
| -x | (Optional) <An array of paths to extension provisioning profiles>. Utilize this if your app needs extension provisioning profiles. |
| -b | (Optional) Apply -b without an argument if y'all want the wrapped output app to take the aforementioned bundle version every bit the input app (not recommended). Use |
| -citrix | (Optional) Include the Citrix XenMobile App SDK (network-only variant). You must accept the Citrix MDX Toolkit installed to use this choice. |
| -f | (Optional) <Path to a plist file specifying arguments.> Use this flag in front end of the plist file if you choose to use the plist template to specify the rest of the IntuneMAMPackager properties like -i, -o, and -p. See Utilize a plist to input arguments. |
Employ a plist to input arguments
An easy style to run the App Wrapping Tool is to put all the command arguments into a plist file. Plist is a file format like to XML that you can use to input your command line arguments using a course interface.
In the IntuneMAMPackager/Contents/MacOS binder, open up Parameters.plist (a blank plist template) with a text editor or Xcode. Enter your arguments for the following keys:
| Plist key | Type | Default Value | Notes |
|---|---|---|---|
| Input Application Bundle Path | String | empty | Aforementioned every bit -i |
| Output Application Package Path | String | empty | Same as -o |
| Provisioning Contour Path | String | empty | Same equally -p |
| SHA-i Document Hash | String | empty | Same as -c |
| ADAL Authority | String | empty | Same as -aa |
| ADAL Client ID | String | empty | Aforementioned as -ac |
| ADAL Respond URI | String | empty | Same equally -ar |
| Verbose Enabled | Boolean | fake | Same as -v |
| Remove Missing Entitlements | Boolean | simulated | Same as -eastward |
| Foreclose Default Build Update | Boolean | false | Equivalent to using -b without arguments |
| Build String Override | String | empty | The custom CFBundleVersion of the wrapped output app |
| Include Citrix XenMobile App SDK (network-simply variant) | Boolean | imitation | Aforementioned as -citrix |
| Extension Provisioning Contour Paths | Array of Strings | empty | An array of extension provisioning profiles for the app. |
Run the IntuneMAMPackager with the plist equally the sole statement:
./IntuneMAMPackager –f Parameters.plist Post-wrapping
Subsequently the wrapping process completes, the bulletin "The application was successfully wrapped" will exist displayed. If an error occurs, see Error messages for help.
The wrapped app is saved in the output folder you specified previously. You can upload the app to the Intune admin panel and associate information technology with a mobile application management policy.
Of import
When uploading a wrapped app, you can endeavor to update an older version of the app if an older (wrapped or native) version was already deployed to Intune. If you feel an error, upload the app as a new app and delete the older version.
You can now deploy the app to your user groups and target app protection policies to the app. The app will run on the device using the app protection policies you specified.
The master scenarios in which you would demand to rewrap your applications are as follows:
- The application itself has released a new version. The previous version of the app was wrapped and uploaded to the Intune console.
- The Intune App Wrapping Tool for iOS has released a new version that enables key bug fixes, or new, specific Intune application protection policy features. This happens later half dozen-8 weeks through GitHub repo for the Microsoft Intune App Wrapping Tool for iOS.
For iOS/iPadOS, while it is possible to wrap with dissimilar cert/provisioning contour than the original used to sign the app, if the entitlements specified in the app are non included in the new provisioning contour, wrapping will fail. Using the "-e" command-line choice, which removes any missing entitlements from the app, to force wrapping to not fail in this scenario can cause broken functionality in the app.
Some best practices for rewrapping include:
- Ensuring that a different provisioning contour has all the required entitlements equally any previous provisioning contour.
Fault messages and log files
Use the following information to troubleshoot issues you have with the app wrapping tool.
Error letters
If the app wrapping tool fails to finish successfully, 1 of the following error messages volition be displayed in the console:
| Fault message | More than information |
|---|---|
| You must specify a valid iOS provisioning profile. | Your provisioning contour might not be valid. Check to make sure you have the right permissions for devices and that your profile is correctly targeting development or distribution. Your provisioning contour might also be expired. |
| Specify a valid input application name. | Brand sure that the input application name you lot specified is correct. |
| Specify a valid path to the output application. | Brand sure that the path to the output application you specified exists, and is correct. |
| Specify a valid input provisioning profile. | Brand sure you supplied a valid provisioning profile proper noun and extension. Your provisioning profile might be missing entitlements, or you might non have included the –p control line selection. |
| The input application you lot specified was not found. Specify a valid input application name and path. | Make sure your input app path is valid and exists. Make sure the input app exists at that location. |
| The input provisioning profile file you specified was non found. Specify a valid input provisioning profile file. | Make sure that the path to the input provisioning file is valid and that the file you specified exists. |
| The output application binder you specified was not found. Specify a valid path to the output application. | Make sure that the output path you specified is valid and exists. |
| Output app does not accept .ipa extension. | Only apps with the .app and .ipa extensions are accepted by the App Wrapping Tool. Brand certain your output file has a valid extension. |
| An invalid signing certificate was specified. Specify a valid Apple signing certificate. | Make sure you lot've downloaded the right signing document from the Apple developer portal. Your document might be expired or might be missing a public or private cardinal. If your Apple tree certificate and provisioning profile tin be used to correctly sign an app within Xcode, then they are valid for the App Wrapping Tool. Additionally, verify that the signing certificate has a unique name within the host macOS auto's keychain. If there are multiple versions of the same document within the keychain this mistake may be returned. |
| The input awarding you specified is invalid. Specify a valid application. | Make sure you accept a valid iOS application that has been compiled every bit an .app or .ipa file. |
| The input awarding you specified is encrypted. Specify a valid unencrypted application. | The App Wrapping Tool does not support encrypted apps. Provide an unencrypted app. |
| The input application you specified is non in a Position Contained Executable (PIE) format. Specify a valid application in PIE format. | Position Independent Executable (PIE) apps can be loaded at a random retention address when run. This tin can take security benefits. For more than about security benefits, see your Apple tree Programmer documentation. |
| The input app you specified has already been wrapped. Specify a valid unwrapped application. | You cannot process an app that has already been processed by the tool. If y'all want to process an app again, run the tool using the original version of the app. |
| The input awarding y'all specified is not signed. Specify a valid signed awarding. | The app wrapping tool requires apps to be signed. Consult your programmer documentation to learn how to sign a wrapped app. |
| The input application you lot specified must be in the .ipa or .app format. | Only .app and .ipa extensions are accepted by the app wrapping tool. Make sure your input file has a valid extension and has been compiled as a .app or .ipa file. |
| The input app you lot specified has already been wrapped and is on the latest policy template version. | The App Wrapping Tool will non rewrap an existing wrapped app with the latest policy template version. |
| Warning: You did non specify a SHA1 certificate hash. Make sure that your wrapped awarding is signed before deploying. | Ensure that you lot specify a valid SHA1 hash following the –c control line flag. |
Collecting logs for your wrapped applications from the device
Use the following steps to get logs for your wrapped applications during troubleshooting.
- Go to the iOS Settings app on your device and select your LOB app.
- Select Microsoft Intune.
- Toggle the Brandish Diagnostics Console setting to On.
- Launch your LOB application.
- Click on the "Get Started" link.
- Yous tin at present share logs through email or copying them to a OneDrive location.
Note
The logging functionality is enabled for apps that have wrapped with the Intune App Wrapping Tool version 7.i.13 or above.
Collecting crash logs from the system
Your app may be logging useful data to the iOS client device panel. This information is useful when you are having problems with the awarding and need to determine if the event is related to the App Wrapping Tool or the app itself. To retrieve this information, use the following steps:
-
Reproduce the issue by running the app.
-
Collect the panel output by post-obit Apple tree's instructions for Debugging Deployed iOS Apps.
Wrapped apps will also present users the option to send logs direct from the device via email afterward the app crashes. Users tin can send the logs to you to examine and forrard to Microsoft if necessary.
Certificate, provisioning profile, and hallmark requirements
The App Wrapping Tool for iOS has some requirements that must be met in order to guarantee full functionality.
| Requirement | Details |
|---|---|
| iOS provisioning profile | Make sure that the provisioning profile is valid before you include it. The App Wrapping Tool does not bank check whether the provisioning contour is expired when processing an iOS app. If an expired provisioning profile is specified, the app wrapping tool will include the expired provisioning profile, and you lot will not know there is a trouble until the app fails to install on an iOS device. |
| iOS signing certificate | Brand sure that the signing certificate is valid before you lot specify it. The tool does not check whether a document is expired when processing iOS apps. If the hash for an expired certificate is provided, the tool volition process and sign the app, but it will fail to install on devices. Make certain that the certificate provided for signing the wrapped app has a match in the provisioning profile. The tool does not validate if the provisioning profile has a match for the certificate provided for signing the wrapped application. |
| Authentication | A device must have a PIN for encryption to work. On devices to which you have deployed a wrapped app, touching the condition bar on the device will require the user to sign in once more with a piece of work or school account. The default policy in a wrapped app is authentication on re-launch. iOS handles whatsoever external notification (like a phone call) by exiting the app and and then re-launching information technology. |
Setting app entitlements
Before wrapping your app, you can grant entitlements to give the app additional permissions and capabilities that exceed what an app can typically practise. An entitlement file is used during code signing to specify special permissions within your app (for example, access to a shared keychain). Specific app services called capabilities are enabled within Xcode during app development. Once enabled, the capabilities are reflected in your entitlements file. For more information nearly entitlements and capabilities, meet Calculation Capabilities in the iOS Developer Library. For a complete list of supported capabilities, encounter Supported capabilities.
Supported capabilities for the App Wrapping Tool for iOS
| Capability | Description | Recommended guidance |
|---|---|---|
| App groups | Utilize app groups to permit multiple apps to access shared containers and allow additional interprocess communication between apps. To enable app groups, open the Capabilities pane and click ON in App Groups. You can add together app groups or select existing ones. | When using App Groups, use opposite DNS annotation: group.com.companyName.AppGroup |
| Background modes | Enabling groundwork modes lets your iOS app continue running in the background. | |
| Data protection | Data protection adds a level of security to files stored on disk past your iOS app. Information protection uses the built-in encryption hardware present on specific devices to shop files in an encrypted format on deejay. Your app needs to be provisioned to use data protection. | |
| In-app purchase | In-app purchase embeds a store directly into your app by enabling you to connect to the shop and deeply process payments from the user. You can use in-app purchase to collect payment for enhanced functionality or for additional content usable by your app. | |
| Keychain sharing | Enabling keychain sharing lets your app share passwords in the keychain with other apps developed by your team. | When using keychain sharing, utilize reverse DNS annotation: com.companyName.KeychainGroup |
| Personal VPN | Enable personal VPN to allow your app to create and control a custom system VPN configuration using the Network Extension framework. | |
| Push button notifications | Apple Push Notification service (APNs) lets an app that isn't running in the foreground notify the user that it has data for the user. | For push button notifications to work, you lot need to use an app-specific provisioning contour. Follow the steps in the Apple tree developer documentation. |
| Wireless accessory configuration | Enabling wireless accessory configuration adds the External Accessory framework to your project and lets your app prepare MFi Wi-Fi accessories. |
Steps to enable entitlements
-
Enable capabilities in your app:
a. In Xcode, go to your app'southward target, and click Capabilities.
b. Turn on the advisable capabilities. For detailed information near each capability and how to determine the right values, see Adding Capabilities in the iOS Developer Library.
c. Note whatsoever IDs that yous created during the process. These may also be referred to every bit the
AppIdentifierPrefixvalues.d. Build and sign your app to be wrapped.
-
Enable entitlements in your provisioning profile:
a. Sign in to the Apple Developer Member Center.
b. Create a provisioning contour for your app. For instructions, see How to Obtain the Prerequisites for the Intune App Wrapping Tool for iOS.
c. In your provisioning profile, enable the same entitlements that you have in your app. Yous will need to supply the same IDs (the
AppIdentifierPrefixvalues) that you specified during the development of your app.d. Terminate the provisioning profile wizard and download your file.
-
Ensure that you have satisfied all the prerequisites, and then wrap the app.
Troubleshoot common errors with entitlements
If the App Wrapping Tool for iOS shows an entitlement error, attempt the following troubleshooting steps.
| Effect | Cause | Resolution |
|---|---|---|
| Failed to parse entitlements generated from the input application. | The App Wrapping Tool cannot read the entitlements file that was extracted from the app. The entitlements file might exist malformed. | Inspect the entitlements file for your app. The post-obit instructions explain how to do then. When inspecting the entitlements file, check for any malformed syntax. The file should exist in XML format. |
| Entitlements are missing in the provisioning contour (missing entitlements are listed). Repackage the app with a provisioning contour that has these entitlements. | There is a mismatch betwixt the entitlements enabled in the provisioning profile and the capabilities enabled in the app. This mismatch besides applies to the IDs associated with particular capabilities (like app groups and keychain admission). | By and large, y'all can create a new provisioning profile that enables the same capabilities as the app. When IDs between the profile and app don't friction match, the App Wrapping Tool will supervene upon the IDs if information technology is able to. If you even so get this error afterwards creating a new provisioning profile, you tin effort removing entitlements from the app by using the –e parameter (see Using the –east parameter to remove entitlements from an app section). |
Find the existing entitlements of a signed app
To review the existing entitlements of a signed app and provisioning profile:
-
Detect the .ipa file and change its the extension to .zip.
-
Aggrandize the .zip file. This will produce a Payload folder containing your .app packet.
-
Use the codesign tool to check the entitlements on the .app bundle, where
YourApp.appis the actual name of your .app package.:codesign -d --entitlements :- "Payload/YourApp.app" -
Use the security tool to bank check the entitlements of the app's embedded provisioning profile, where
YourApp.appis the actual name of your .app bundle.security cms -D -i "Payload/YourApp.app/embedded.mobileprovision"
Remove entitlements from an app by using the –e parameter
This command removes any enabled capabilities in the app that are not in the entitlements file. If you remove capabilities that are being used by the app, it can break your app. An example of where you might remove missing capabilities is in a vendor-produced app that has all capabilities past default.
./IntuneMAMPackager/Contents/MacOS/IntuneMAMPackager –i /<path of input app>/<app filename> -o /<path to output folder>/<app filename> –p /<path to provisioning profile> –c <SHA1 hash of the certificate> -eastward Utilise the following security and privacy best practices when you apply the App Wrapping Tool.
-
The signing certificate, provisioning profile, and the line-of-business app you specify must exist on the same macOS machine that you lot utilize to run the app wrapping tool. If the files are on a UNC path, ensure that these are accessible from the macOS machine. The path must exist secured via IPsec or SMB signing.
The wrapped application imported into the admin panel should be on the aforementioned computer that you run the tool on. If the file is on a UNC path, ensure that it is accessible on the computer running the admin console. The path must be secured via IPsec or SMB signing.
-
The environment where the App Wrapping Tool is downloaded from the GitHub repository needs to be secured via IPsec or SMB signing.
-
The app you procedure must come from a trustworthy source to ensure protection against attacks.
-
Ensure that the output folder you specify in the App Wrapping Tool is secured, particularly if information technology is a remote folder.
-
iOS apps that include a file upload dialog box can allow users to circumvent, cutting, copy, and paste restrictions practical to the app. For example, a user could utilise the file upload dialog box to upload a screenshot of the app data.
-
When you monitor the documents folder on your device from within a wrapped app, yous might see a binder named .msftintuneapplauncher. If you modify or delete this file, it might affect the right performance of restricted apps.
This characteristic is an integration with the Citrix MDX app wrapper for iOS/iPadOS. The integration is simply an boosted, optional command-line flag, -citrix to the general Intune App Wrapping Tools.
Requirements
To use the -citrix flag, yous will also need to install the Citrix MDX app wrapper for iOS on the same macOS machine. The downloads are found on Citrix XenMobile Downloads and are restricted to Citrix customers only afterwards signing in. Make sure this is installed in the default location: /Applications/Citrix/MDXToolkit.
Note
Support for Intune and Citrix integration is express to iOS 10+ devices simply.
Use the -citrix flag
Simply run your full general app wrapping command and with the -citrix flag appended. The -citrix flag currently does non have any arguments.
Usage format:
./IntuneMAMPackager/Contents/MacOS/IntuneMAMPackager -i /<path of input app>/<app filename> -o /<path to output folder>/<app filename> -p /<path to provisioning profile> -c <SHA1 hash of the certificate> [-b [<output app build string>]] [-five] [-due east] [-ten /<assortment of extension provisioing contour paths>] [-citrix] Example control:
./IntuneMAMPackager/Contents/MacOS/IntuneMAMPackager -i ~/Desktop/MyApp.ipa -o ~/Desktop/MyApp_Wrapped.ipa -p ~/Desktop/My_Provisioning_Profile_.mobileprovision -c 12A3BC45D67EF8901A2B3CDEF4ABC5D6E7890FAB -5 truthful -citrix See too
- Decide how to set apps for mobile application management with Microsoft Intune
- Common questions, issues, and resolutions with device policies and profiles
- Use the SDK to enable apps for mobile application management
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/mem/intune/developer/app-wrapper-prepare-ios
0 Response to "Messenger Upload Failed Make Sure You Are Uploading a Valid File -photo"
Post a Comment